Part IV: Wireless Security Technologies
“Devising a network security policy can be complex because a rational policy requires an organization to relate network and computer security to human behavior and to assess the value of information.” – Douglas E. Comer, professor at Purdue University. (Comer, 2004, p. 608)
When wanting to provide security to a certain working environment, it’s good to evaluate what are the threats to such environment. Same is with networking security, including here wireless networks. It’s very important to asses which are the threats to your wireless network, so you implement the best possible security. According to the Webster dictionary, security is defined as the condition or quality of being free from apprehension, anxiety, or care. In relation to the definition of security and secured network, Chandra (2005) says “a secure communication network, then, can be defined as a network whose users do not feel any apprehension or anxiety while using the network” (p. 1). In real life, we notice different security technologies implemented with a purpose to secure networks. But is the threat coming always from outside, or that’s more than that? Besides threats coming from outside in organized way, there is a lot of possibility in an intentional or unintentional format possible threats to be generated from inside of the perimeter network. Often, we hear how a user mistakenly did compromise the security of its corporate network; or situation when the unknown flaws in a certain application software caused to ruin down several services inside of a perimeter network, or even shutting down the entire network. According to Pfleeger & Pfleeger (2003) “in large networks, a huge number of potential attackers can probe the software extensively; the result is that a network often includes many identified faults and software patches to counter them” (p. 480). With this said humans and systems responsible for providing security for computer networks including wireless networks as well, should always be open eye and in a standby mode.
Can computer networks based on the security implemented in them be classified as secured or not secured? An answer to this question is coming from Comer (2004) who says that “although the concept of a secure network is appealing to most users, networks cannot be classified simply as secure or not secure because the term is not absolute – each organization defines the level of access that is permitted or denied” (p. 607). Than in particular what is and what can contain a security in the network? Pfleeger & Pfleeger (2003) are saying that “in a sense, security in networks is the combination and culmination of everything we know about security” (p. 480). Furthermore, “a network’s security depends on all the cryptographic tools at our disposal, good program development processes, operating system controls, trust and evaluation and assurance methods, and inference and aggregation controls” (Pfleeger, 2003, p. 480).
At the beginning of this section, I have said that in order for the company to implement a security inside of the perimeter network, is required an assessment of threats to that perimeter network. With this, and the other fact that from the point of security computer networks cannot be classified as secured and non-secured, then the very first step an organization needs to do is the process of defining company’s security policy. In relation to what exactly security policy is, Comer (2004), is saying that “the security policy does not specify how to achieve protection, instead, it states clearly and unambiguously the items that are to be protected” (p. 608).
Knowing few of the existing threats and attacks to wireless networks, including here also its open networking nature, wireless technology, by its nature, “violates fundamental security principles” (Nichols, & Lekkas, 2002, p. 1). Furthermore, Nichols & Lekkas (2002) are saying that “wireless technology does not ensure the identity of the user and the device (authentication), nor prevent the sender of the message from denying he or she has sent it (nonrepudiation)” (p. 1). Form the very first section of this paper; we have learned that while wireless communication “is as old as the human civilization itself”, in contrast to this wireless technology is solidly new. With this said, whenever deciding to design and implement wireless network than its good to know that “wireless technology opens up the possibility of security breaches” (Mueller, 2004, p. 290). In the following lines, will be explored the security mechanism available in today’s wireless technology.
Wired Equivalent Privacy (WEP) – designed and developed to protect IEEE 802.11 wireless networks, known differently Wireless-Fidelity networks. “WEP is part of the IEEE 802.11 standard, ratified in September 1999” (Wikipedia, 2016, ¶ 3). Its development and than its implementation, was supposed to provide comparable confidentiality to a traditional wired network. It means that, the responsibility of the WEP was to provide security for wireless networks, to similar fashion as the security for wired networks. WEP offers confidentiality by using the stream cipher RC4, and offers integrity by using the CRC-32 checksum. Besides confidentiality and integrity, WEP offers also authentication. Fleck & Potter (2002) are saying that “the key that a client is using for authentication and encryption of the data stream must be the same key that the AP uses.” In WEP, packets are encrypted when an RC4 stream is generated. Thus, to achieve encryption a significant role in WEP plays RC4 stream cipher in combination with 24-bit initialization vector (IV) and a shared key. The answer to question such as: why 24-bit initialization vector (IV) is used in WEP, is provided by Maxim & Pollino (2002), that are saying that “the IV is used to make the RC4 stream generated with the shared key different for many of the data transmissions, then the data is XORed with the generated stream and transmitted in a WEP frame with the IV in the header so the receiver can generate the same RC4 stream to XOR the packet for decryption” (p. 75).
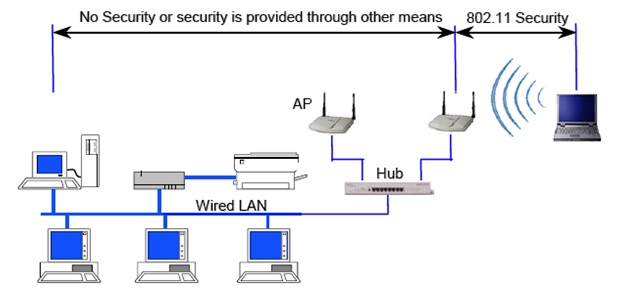
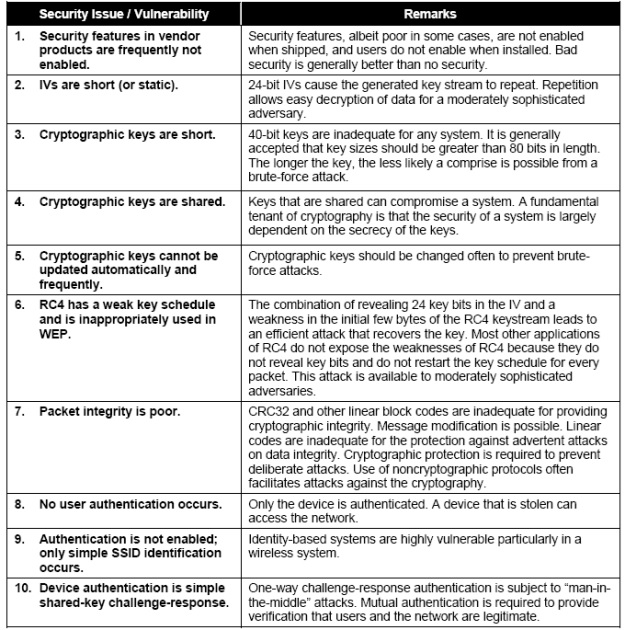
According to Mueller (2004), “the first version of WEP, standard 64-bit WEP, used a simple 40-bit encryption key which was implemented in both Access Point (AP) and the wireless client.” Although, WEP solely was designed to be security mechanism for protecting wireless networks, in real life it did not prove to be that way. Up-to-date are registered several serious weaknesses with WEP, which in turn does not rates it as a security mechanism that provides high security. With few words, it can be said that WEP is not providing protection to wireless networks, instead is slowing down the attacks to wireless networks. In relation to what type of security WEP is providing in wireless network, Karygiannis & Owens (n.d.) are saying that “WEP does not provide end-to-end security but only for the wireless portion of the connection” (p. 3-6). An attempt to enhance security within the WEP was made through the process of increasing key size from standard WEP 64-bit to extended WEP 128-bit. But, for some period of time extended WEP 128-bit couldn’t be implemented by manufacturers of wireless technology, because US Government export restrictions on cryptographic technology limited the key size. After such restriction was lifted, almost all the manufacturers have started to include extended WEP 128-bit in wireless technologies. In reality, the extended WEP 128-bit is using 104-bit key size. While, Figure1 is showing Wireless security of 802.11b in typical network, Figure2 is showing summarized problems of WEP and 802.11b WLAN security:
Figure1: Wireless security of 802.11b in typical network (Karygiannis, Owens, n.d.).
Wired Equivalent Privacy 2 – was introduced by Wireless Ethernet Compatibility Alliance (WECA) in order to increase furthermore the security in wireless networks, especially after almost ‘failing’ with WEP. WEP2 is not a new wireless security mechanism in its entirety, instead represents an improved WEP. Significant improvements are made through extending the key size from standard WEP of 64-bits, to extended WEP (or WEP2) of 128-bits. Stark (2001) adds to it ““WEP2 does increase the IV key space to 128 bits, but it fails to prevent IV replay exploits and still permits IV key reuse” (¶ 20). Although, quite enhanced in his architecture, WEP2 in reality proved to inherit weaknesses of its big brother WEP. Gast (2002) adds “WEP, however, is not a well-designed cryptographic system, and the extra bits in the key buy you very little” (p. 76). In similar fashion, is capable of slowing down the attacks, but not protecting the wireless network. Reason for it is provided by Stark (2001) who says that “WEP2 is being designed to be downwardly compatible with and to interoperate with WEP1, thus many engineers think that’s a major architectural blunder, because WEP1 simply wasn’t designed for security from the ground up, and to meet the IEEE’s goal of interoperability, WEP2 will have to be built on that same, insecure foundation” (¶ 27).
Figure2: Summarized problems of WEP and 802.11b WLAN security (Karygiannis, Owens, n.d.)
Wired Equivalent Privacy plus – sometimes known as WEP+, represents proprietary enhancement made to WEP by accompany Agere Systems, Inc. (http://www.agere.com/). Significant enhancement in WEPplus is the fact that through the ‘Weak Key’ method of attack it reduces vulnerability in wireless networks. In real world, WEPplus increased considerably the security in wireless networks. Thus, to my understanding the secret of success lies in its nature, i.e. WEPplus is a proprietary security mechanism, and not an open standard. In terms of WEPplus implementation, Young (2004) says the following: “the WEPplus implementation provides complete inter-operability with all Wi-Fi compliant Wireless LAN products, offering complete interoperability of Wireless LAN equipment across different vendors” (¶ 7).
Dynamic Wired Equivalent Privacy – known shortly as dynamic WEP, represents another proprietary security scheme in wireless technology. Because dynamic WEP changes the keys dynamically, therefore is not using static keys like a WEP, then that proves to be where the name is coming from. Dynamic WEP in its uniqueness represents the combination of a wireless technology such as 802.1x, and authentication technology such as Extensible Authentication Protocol. In terms of the process of generating keys in dynamic WEP, according to Rittinghouse & Ransome (2004) “each time a user logs into the network, a new key is created for that session, thus other user will have the same session key, and the key lengths are such that reuse of the keys would be impossible to predict.” This approach increases security in dynamic WEP in comparison to standard WEP.
Service Set Identifier (SSID) – which is thought to be additional security mechanism, that provides security for wireless networks. But Mueller (2004) has different opinion in regard to the role of the SSID in wireless networks; he says “SSID is a component of wireless technology, believed by the majority of home users as wireless networking security tool, is not providing security for wireless network, instead, the SSID is simply used to separate wireless networks” (p. 348). So, how SSID looks like and where is located? According to Rittinghouse & Ransome (2004), “the SSID is a 32-character unique identifier attached to the header of packets sent over a WLAN.” One thing is for sure, in its originality, wireless network administrators are benefiting a lot from SSID.
Wi-Fi Protected Access (WPA) – has been created in order to overcome the weaknesses and criticism of the WEP. The owner of the WPA is Wi-Fi Alliance. WPA it’s a wireless security mechanism that intends to take the place of the WEP. Whenever WPA is mentioned, immediately our mind goes to 802.11i wireless standard, which is implemented in its entirety by WPA. WPA exists in two modes: WPA Enterprise Mode designed to utilize the 802.1x authentication server; and WPA Pre-Shared Key Mode designed for home usage who can not afford the cost and complexity of 802.1x authentication server. A similarity can be drag in between WPA and dynamic WEP, if not in terms of level of security provided by both, then at least in the way they work. This means that, WPA in order to prevent unauthorized access to a wireless network uses the encryption technology for authentication process; and WPA uses changing key which changes constantly. WPA is designed to work with all wireless network interface cards, but not necessarily with first generation wireless access points (Wikipedia, 2016, ¶ 1). WAP, same as WEP is using the RC4 stream cipher in order to encrypt data. The size of the key is 128-bits, and the size of the initialization vector (IV) is 48-bit. According to Wikipedia (2007), ““one major improvement in WPA over WEP is the Temporal Key Integrity Protocol (TKIP), which dynamically changes keys as the system is used, which when combined with the much larger IV, this defeats the well-known key recovery attacks on WEP” (¶ 4).
Wi-Fi Protected Access 2 (WPA 2) – represents the second version of Wi-Fi Protected Access which was reshaped and restructured in order to increase the security in wireless networks. Comparing to WPA, WPA 2 uses AES encryption algorithm, and uses 802.1x based authentication. Similar as WPA, also WPA 2 exists in two modes: WPA2 Enterprise, which verifies network user through the usage of a server; and WPA2 Personal which by utilizing a set-up password protects wireless network from unauthorized access. According to Wikipedia (2016) starting as of “March 13, 2006, WPA2 certification is mandatory for all new devices wishing to be Wi-Fi certified’ (¶ 8).
Wireless Transport Layer Security (WTLS) – represents the security layer for Wireless Application Protocol (WAP) in wireless data network. According to Maxim & Pollino (2002) “WTLS was designed specifically because the low-bandwidth and hardware limitations of cellular handsets made implementing wireless SSL technically challenging” (p. 23). WTLS is based upon TLS security layer used widely in the Internet, which had gone through the modification in order to support the low-bandwidth of wireless communications.
Wireless VPNs – means creating private secure paths over wireless network infrastructure. Knowing that the Internet is comprised of combined networking infrastructures such as wired and wireless, and the fact that there is more and more increasing the trend of exchanging data from the Internet to private networks, and back & forth; then its necessary to establish VPNs in wireless networks whenever a data transportation process takes places in between the Internet and wireless network, and reverse. There is a strong reason behind the decision to use VPNs in wireless networks, its all about encryption and authentication that VPNs are using in their activity of transmitting data. VPN servers are essentially encrypting routers that provide authentication support. With this said, according to Rittinghouse & Ransome (2004), “mobile users can use wireless VPNs to securely access a corporate network from remote locations such as a wireless hotspot or from segmented parts of the LAN behind an enterprise wireless gateway or firewall device.” Besides encryption and authentication, VPNs provide data privacy as well. Thus, based on Rittinghouse & Ransome (2004), “VPNs have an advantage over other solutions because they consist primarily of resources that are already in place and that can be enhanced by VPN hardware products, software packages, or both.”
IP Security (IPSec) – it’s a security mechanism that was developed by IETF which is responsible of providing security at Internet Protocol layer. In terms of implementation, Maxim and Pollino (2002) are saying “the most common implementations of IPSec are using a tunnel mode that enables all IP traffic to be encrypted and optionally authenticated inside a single session” (p. 77). This type of implementation brings up thinking that IPSec is everywhere when VPN is also. Because of its wide range usage in terms of providing security when it comes to transmission of data in public network, therefore IPSec represents a first choice to be used in wireless networks for securing wireless applications.
In Conclusion
Today, security is first priority of each organization when it comes to designing and implementing computer networks with an aim to set up and provide networking services. Among computer networks, significant percentage make up wireless networks, which now days is not only a trend, but a demand. With this said, regardless of the level of the security that today’s available security mechanism in wireless technology are able to provide, the need for being able to communicate and transmit data while on the go, is driving forward the expansion of wireless networks. Along with it, security in this area of networking will and must improve furthermore.
Hmmm! Yes, this expansion will move on in the years to come in the future.
References:
Chandra, Praphul. Bulletproof Wireless Security GSM, UMTS, 802.11, and Ad Hoc Security. Oxford, UK: Elsevier, Inc., 2005.
Comer, Douglas E. Computer Networks and Internets with Internet Applications, 4th Ed. New Jersey: Prentice Hall, 2004.
Fleck, Bob & Bruce Potter. 802.11 Security. California: O’Reilly, December 2002.
Gast, Mathew. 802.11® Wireless networks: The Definitive Guide. California: O’Reilly, April 2002
Karygiannis, Tom & Les Owens. DRAFT: Wireless Network Security 802.11, Bluetooth and Handheld Devices. Gaithersburg, MD: NIST, n.d.
Merritt, Maxim & David Pollino. Wireless Security. McGraw-Hill Companies, Inc., 2002.
Mueller, Scott. Upgrading and Repairing Networks, 4th Ed. Indianapolis: QUE Publishing, 2004.
Nichols, Randall K. & Panos C. Lekkas. Wireless Security Models, Threats, and Solutions. McGraw-Hill Companies, Inc., 2002.
Pfleeger, Charles, & Shari Lawrence Pfleeger. Security in Computing, 3rd Ed. New Jersey: Prentice Hall, 2003.
Publication Manual of the American Psychological Association, 5th Ed. Washington, D.C.: American Psychological Association 2001
Rittinghouse, John & James Ransome. Wireless Operational Security. Oxford, UK: Elsevier, Inc., 2004.
Stark, Thom, 2001. “It Came Out of the Sky WEP2, Credibility Zero.” Retrieved on December 07th, 2016 from URL: http://www.starkrealities.com/wireless003.html
Wikipedia, 2 December 2016. “Wi-Fi Protected Access.” Retrieved on December 10th, 2016 from URL: http://en.wikipedia.org/wiki/Wi-Fi_Protected_Access
Wikipedia, 1 December 2016. “Wired Equivalent Privacy.” Retrieved on December 10th, 2016 from URL: http://en.wikipedia.org/wiki/Wired_Equivalent_Privacy
Young, Michael F, 2004. “WEPplus from Agere.” Retrieved on December 11th, 2016 from URL: http://www.terabeam.com/solutions/whitepapers/wep-plus.php
Hope you’ll find this post informative.